- How to: SSH into your webhost using cPanel credentials through Linux Console
- SSH to WebHost using public/private SSH keys login generated by cPanel
- Howto: Generate SSH Keys on your local computer and use with the Server
- System, Network & Disk management Linux commands you should know to manage your web server
- Common directory and file management commands in Linux
- User and Group Management in Linux – System Administration & Advanced Concepts
- Understand File and Directory Permissions in Linux – Concept and Viewing
- Change File and Directory Permissions in Linux – Terminal Commands
Last time we talked about Groups and Users in a standard Linux system. Now comes one of the practical implementation of Group and User concept, ie, File and Directory permissions in Linux. There is a lot we can do with files and directories, and if the permission is not set properly, then either your application can fail to run, or your files will become vulnerable to security threats. So, it is not only important to understand the concepts of File & Directory Permissions, rather, is mandatory if you want to successfully administrate a Linux system.
Please note that this tutorial assumes, you have the understanding of Group & User concepts. If not, then we recommend reading this tutorial to get you started. The examples here also uses concepts of paths. So please read about common directory and file related commands if you are not familiar with paths.
#0: Basic Concepts:
 Everything in Linux is a file. It includes normal files, links, directories and all other possibilities. Now, every file should have its own permission sets. The permission bits written within a file, tells the Linux system, which users should be able to perform specific operations on a file.
Everything in Linux is a file. It includes normal files, links, directories and all other possibilities. Now, every file should have its own permission sets. The permission bits written within a file, tells the Linux system, which users should be able to perform specific operations on a file.
While talking about operations, it differs for different file types, specifically for normal files and directories. So, let us see first, what operations we can perform on specific types of files.
#0.1: Operations to Perform:
Before we proceed, let us quickly discuss the three types of operations first. All of these operations are represented either using symbols or octal numbers (we are coming to this shortly). These operations are mainly: read, write and execute. The outcome of these operations are quite understandable from their name itself, but in practice though, it differs a bit. We shall see them next.
List of Permissions based on Operation:
| Operations | Representations | Effects on | ||
|---|---|---|---|---|
| Symbolic | Octal | Files | Directories | |
| Read | r | 4 | Affected users can Read the file. | Affected users can list the files within the directory. |
| Write | w | 2 | Affected users can modify the file. | Affected users can create, rename or delete files inside the directory and modify the directory’s attributes.So, if a file has Write bit set, then we can only edit that file, but we will be able to rename or delete it, only if the parent directory has write permission. |
| Execute | x | 1 | The file can be executed by the affected users. For example a script or an application file. | Affected users can enter the directory and access files and directories inside.Note that, a directory must have both Read and Execute permission in order to let proper access to all the files inside it. With just execute permission, the affected users can access the directory, but can not list files within it. |
| No Permission | – | 0 | None of the above operations can be performed by the affected users. | |
So, we see that, on every file (be it a normal file or a directory), we can perform three types of operations. Obviously, the next question which comes to mind is, who can perform these operations. Let us see…
#0.2: Understanding Ownerships:
Every file (again, including directories) is owned by a specific User and a specific Group. All other users (not even falling under the specified group) are referred as “Other”. So, permissions are set separately for these three.
- User: The user to which the file belongs. Usually the user who creates the file, becomes its owner.
- Group: The group to which the file belongs. Usually, the primary group of the owner (user) becomes the owner group of the file.
- Other: Every other users who is neither the owner nor a member of the owning group are referred as other.
It is important to separately set permission to each of the ownership. If we do not however, then it is treated as “No Permission”.
#1: Viewing File Permissions in Linux:
At this point, we know that a file has three owners and each of the owner will have its own permission. Now we shall see, how to view the permissions of a particular file. In general, the ls command with l parameter is used.
#1.1: To view permission of everything inside a directory:
If present working directory, then we use:
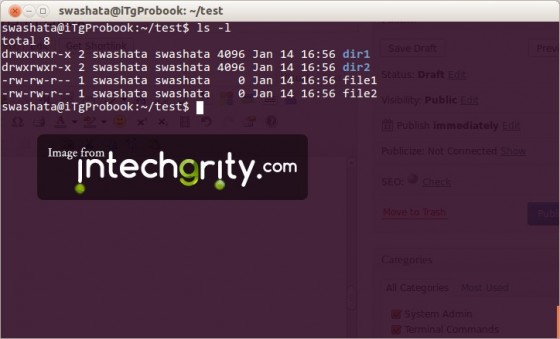
ls -l
The output is something like this.
Or we can also specify the path (absolute or relative) of a directory:
ls -l /home/swashata/test/dir1
Similarly, the new output becomes:
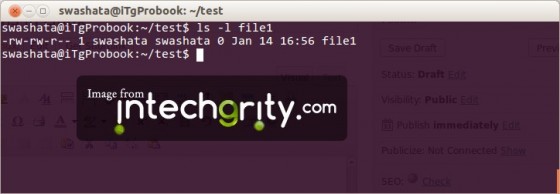
#1.2: To view permission of a file:
The command ls is used with l parameter.
ls -l directory/file
The command above would output something like this:
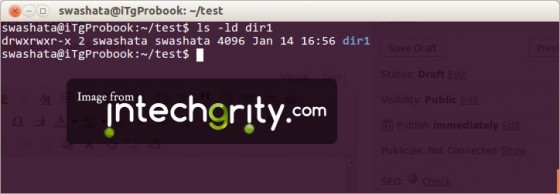
#1.3: To view the permission of a directory:
The command ls is used with l and d parameter.
ls -ld dir1
And the output:
#1.4: Understanding the output:
Let us first see the output of the ls -l command.
drwxrwxr-x 2 swashata swashata 4096 Jan 14 16:56 dir1 drwxrwxr-x 2 swashata swashata 4096 Jan 14 16:56 dir2 -rw-rw-r-- 1 swashata swashata 0 Jan 14 17:15 file1 -rw-rw-r-- 1 swashata swashata 0 Jan 14 16:56 file2
It is split into 7 columns which gives the following informations:
- Column 1 gives the information on file type and permissions.
- Column 2 gives the number of hardlinks.
- Column 3 gives the Username of the User owning the file.
- Column 4 gives the Groupname of the Group owning the file.
- Column 5 gives the I/O block size.
- Column 6 gives the date and time at which the file was last modified.
- Column 7 gives the name of the file.
Everything except the 1st column is easy to understand. So let us take a closer look inside the 1 columns.
As we can see, the first column has 10 characters, which can be split into 4 groups. See the table below to understand.
| Group 1 | Group 2 | Group 3 | Group 4 | |
|---|---|---|---|---|
| Length of Characters | 1 | 3 | 3 | 3 |
| Explanation | Shows the file type. Possible characters are:
|
Permission of the User in symbolic representation. If the permissions allows all three operations, then it would be rwx, if it allows only read, then it would be r–, similarly if it allows read and execute, then r-x | Permission of the Group in the same format. | Permission of Other in the same format. |
| Example |
d |
rwx |
rwx |
r-x |
| Interpretation | The file is a directory | User has Read, Write and Execute Permissions. | Group has Read, Write and Execute Permissions. | Other has only Read and Execute Permission. |
| Example |
- |
rw- |
rw- |
r-- |
| Interpretation | The file is a regular file. | User has Read and Write Permissions. | Group has Read and Write Permissions. | Other has only Read permission. |
Still have questions? Just ask through the comments.
#2: Understanding Sticky bits of directories:
By default, if a directory has the permission bits:
rwx rwx r-x
Then, other users apart from the Owner can delete/rename files inside the directory. But in case of some special directories, like /tmp directories, we would want to avoid deletion by other users than the owner. To support this, the sticky bit concept was introduced.
If a directory has a sticky bit, then all files and directories inside it can be modified (rename and/or delete) only by the owner of the file/subdirectory or the superuser.
If we do a simple
ls -ld /tmp
Then the output would be
drwxrwxrwt 11 root root 4096 Jan 14 17:17 /tmp
Note the extra character “t” added at the end of the first column which shows the sticky bit.
Few interesting cases:
- If one has (write+execute) permission on a directory, then one can rename/delete a file inside that directory even if the user does have write access to that file.
- If we give only write and execute (but not read) permission to a directory, then we will not be able to list the files inside that directory. But if we are aware of the files, then we can edit/read/execute the file if corresponding permissions are set. This gives a useful way to protect a directory from unauthorized listing.
References:
- http://www.tuxfiles.org/linuxhelp/filepermissions.html
- http://unix.stackexchange.com/questions/21251/why-do-directories-need-the-executable-x-permission-to-be-opened
- http://stackoverflow.com/questions/790686/understanding-linux-directory-permissions-reasoning
So, that’s all for now. Next on this series will discuss on commands like chown, chgrp and chmod to explain how we can modify the Owner and Permissions of a file.